Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the operational risks, and how are they assessed?
The problem domain of cyber resilience is so complex and dynamic that it is difficult to imagine where to begin. What practical steps ensure fiduciary responsibilities to both stakeholders and the broader community at large? It is high-level questions like these that have significant system design and operational process ramifications.
Fortunately, resources are available that can guide companies toward a robust cybersecurity strategy.
Government Resources Implemented to Combat Cybersecurity Vulnerabilities
What is needed is an industry-standard formal methodology that deals with assessing and implementing industrial control system cybersecurity. The U.S. and U.K. governments are well on the way to developing such resources.
CISA (Cyber Security and Infrastructure Security Agency): The USA
The U.S. Government created the Cyber Security and Infrastructure Security Agency (CISA) in 2018. It is a component of the Department of Homeland Security, purposed with the mission of reducing threats to the critical physical and cyberinfrastructure – including industrial control systems. Risks and solutions are organization-specific, and CISA has structured approaches relating to business size and the importance of its activity to national security.
The U.S. government is building a vast resource for organizations to utilize. Small to mid-sized businesses may find CISA’s “Cyber Essentials” guide and Cyber Security Resources Road Map (specifically for critical infrastructure small business) as a great place to start in the right direction. The guide focuses upon building a culture of cyber readiness in the company in a holistic strategy that incorporates staff, systems and importantly – how to limit damage and restore operations promptly. There is a functional emphasis on managing physical access, multi-factor authentication, and management of change, including upgrade and bug fixes.
CPNI (Centre for the Protection of National Infrastructure): The UK
The U.K. government has instituted a government authority for protective security advice to U.K. national infrastructure that is directly accountable to the director of MI5, called the Centre for the Protection of National Infrastructure (CPNI). They direct those responsible for industrial control systems to the National Cyber Security Centre’s (NCSC) ten-step guide to cybersecurity which deals with the practicalities of implementing secure systems.
There are specific guidelines for small businesses and large organizations that include ‘Exercise in a Box’, an online tool intended to help companies discover how cyber resilient they are and practice response to cyber events. Sometimes the disconnect between levels in an organization can hinder progress. The NCSC and a board toolkit that focuses on encouraging discussion between the directors and their technical experts.
Cyber Resilience Review
Larger businesses are encouraged to carry out a more extensive effort. CISA has established a standardized ‘Cyber Resilience Review’ (CRR) resource that focuses on a self-assessment process based on the CERT Resilience Management Model (CERT-RMM) developed by Carnegie Mellon University. They also have a list of recommended practices intended to facilitate understanding of and prepare a response to emerging cybersecurity issues and vulnerabilities.
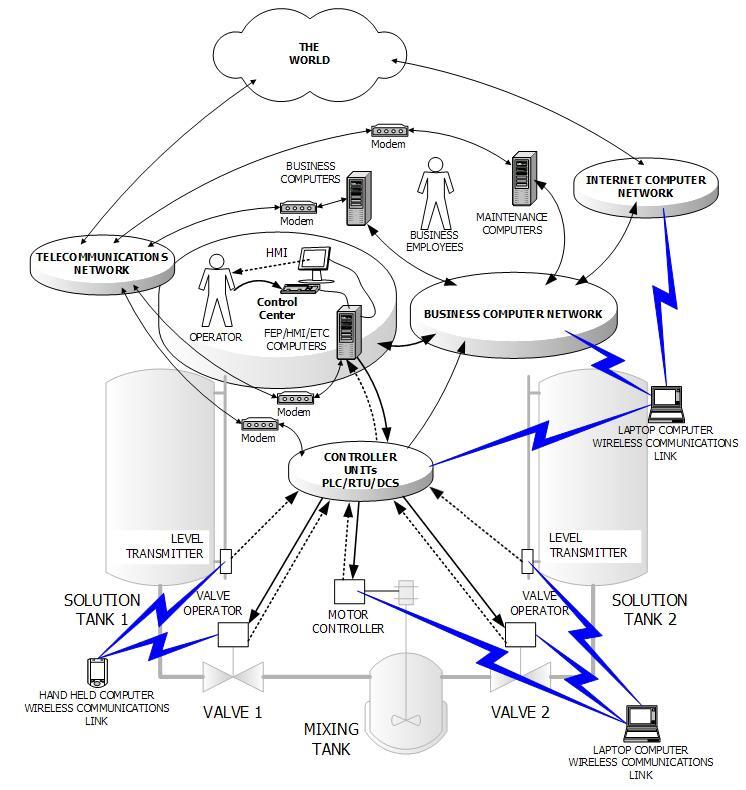
Communications access to control systems. Image from CISA. Click to enlarge.
The Industrial Control Systems Computer Emergency Readiness Team (Industrial Control Systems Security) recommended practices include defense strategies, forensics, and incidence response methods. The mitigation strategies also factor in advice on secure system design and make a detailed exploration of potential attack paths.
The resource material covers various aspects of an industrial control system in detail, with multiple topologies broken down and analyzed as shown in the central figure on the page. The resources explore architectures with SCADA systems and different LAN/ Firewall arrangements, along with the exploration of attacker strategies like ‘man in the middle’ attacks.
The Cyber Resilience Toolbox
Going well beyond this, CISA deals with the system design fundamentals directly, with comprehensive resources specifically on secure architectural design. The highly detailed infographic presented on the webpage has an underlying hierarchical structure; hover over the elements depicted and a box will pop up with links to underlying definitions and documentation.
Over and above this, a highly detailed paper from the Industrial Control Systems Cyber Emergency Response Team is available for download which covers the ‘Recommended Practices for Industrial Control Systems with Defence–in–Depth Strategies.’ This document points out that although the concept of Defence in Depth is not new, many companies do not apply it to their control system operations as they mistakenly do not see a need to do so.

The paper from the Industrial Control Systems Cyber Emergency Response Team is available for download for free.
This position came from the control system legacy of obscure protocols widely considered “hack-proof” due to their separation from the cloud and due to physical protection measures already in place. As control architectures are increasingly networked, recent high-profile intrusions have highlighted the potential risk to control systems. Because of the complexity of control system architectures, and the myriad of different vulnerabilities and exploits, it is essential to establish a layered, multitier strategy.
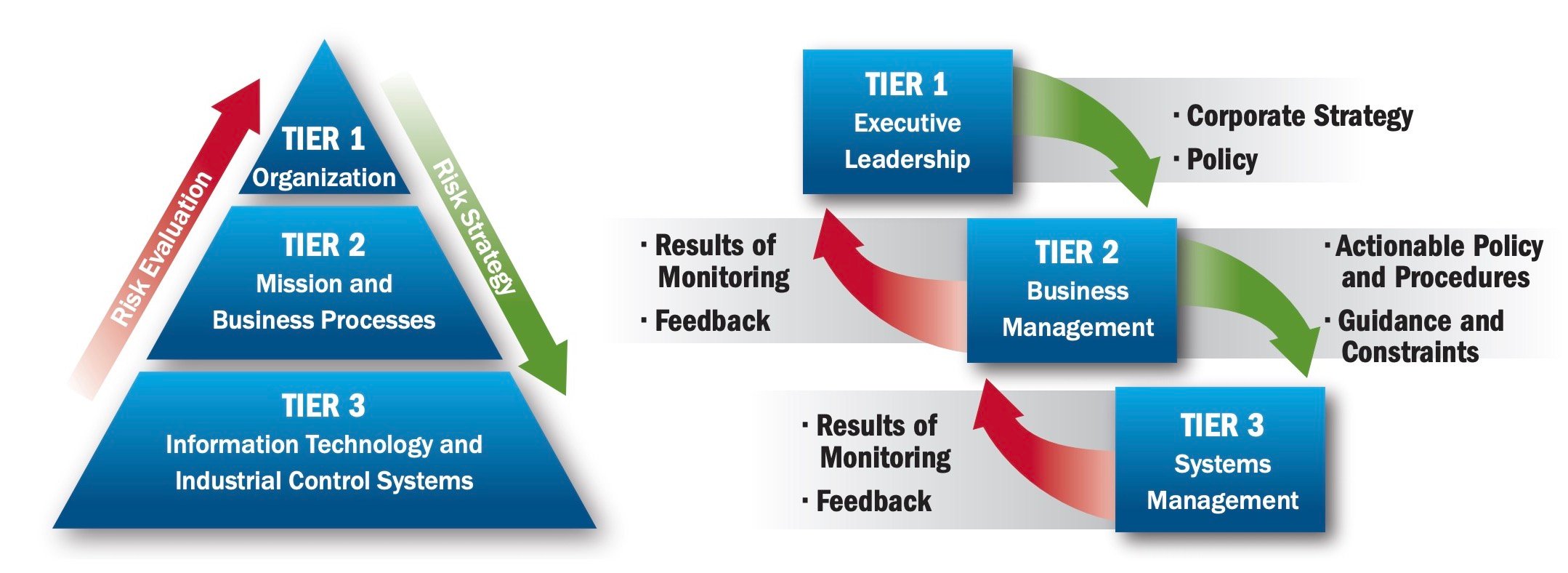
A structure of a multitier cyber resilience strategy from CISA
Upgrading Isolated Control System Networks
A significant challenge for any organization is merging the existing IT architecture with an isolated control system network that may not have countermeasures in place.
From a simplistic TCP/IP connectivity perspective, the protections in the IT routers and firewalls may seem sufficient and an obvious strategy. However, unauthorized access of the corporate IT network could in turn, immediately compromise the control system integrity. A bad actor—or even complications due to application bugs—could create havoc, and relying upon the existing cybersecurity assumes the control systems do not have higher requirements for isolation due to their criticality and may require a completely different authentication system.
The diagram ‘Recommended Secure Network Architecture’ is an integrated architecture example provided by the International Society of Automation (ISA) that includes external interconnections to corporate LAN and various sites on the Internet and is based upon the ISA-99 (Purdue) Model of Control:
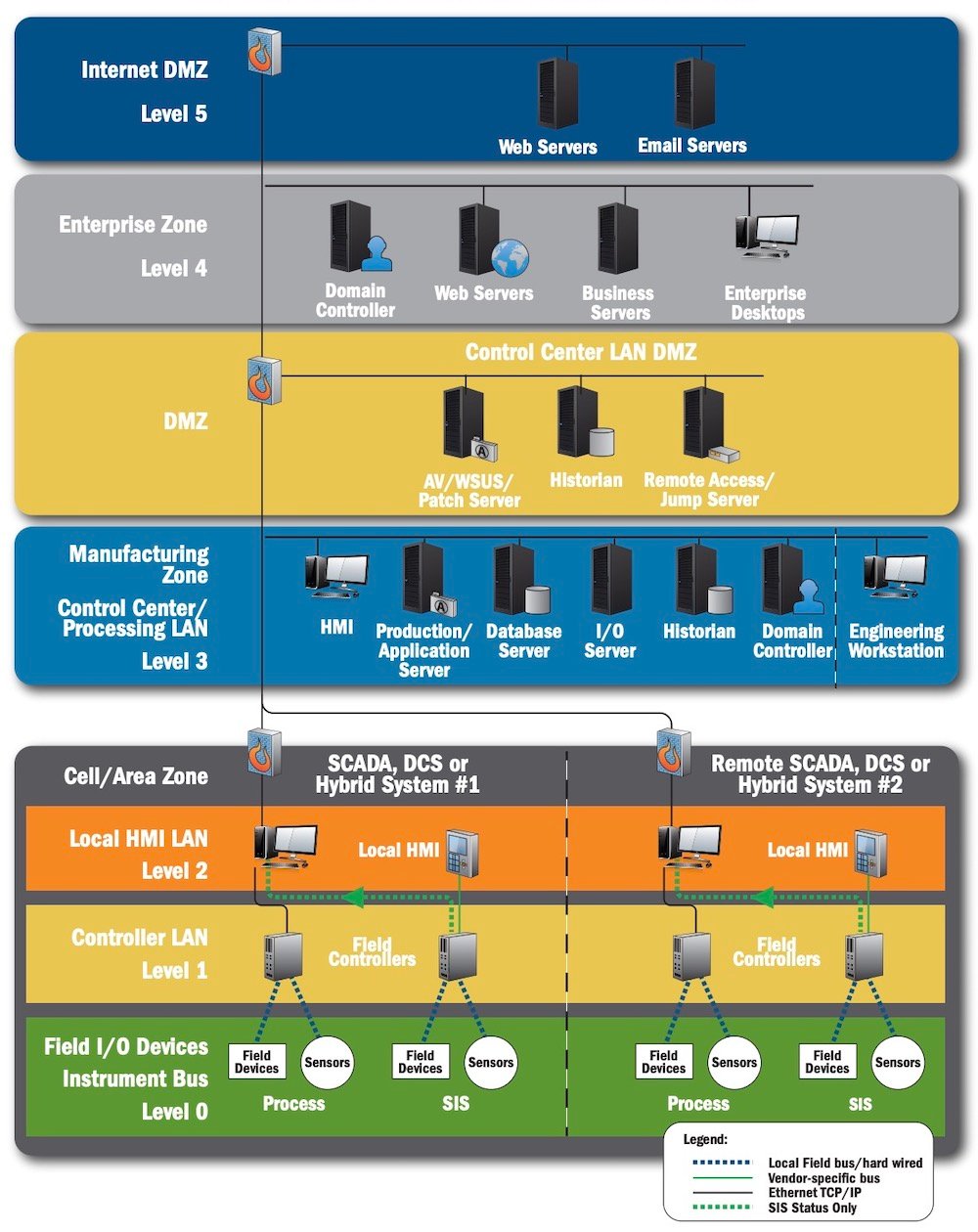
The “Recommended Secure Network Architecture” example from CISA. Click to enlarge
Cyber Resilience Strategy
In preparing a cyber resilience strategy, it is essential to bear in mind the fundamental security function differences between the existing IT infrastructure and a control system. The book mentioned above has a summary comparison table that helps understand these differences.
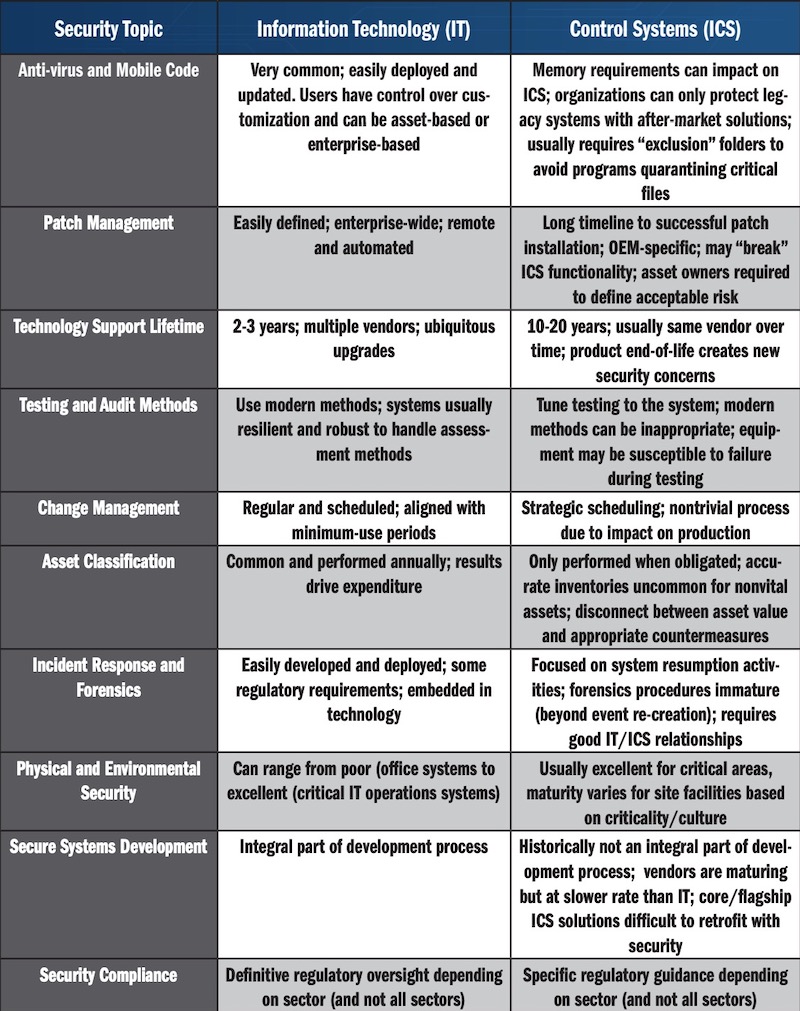
The security functions table from CISA.
It serves to clearly show that it’s pointless considering cyber defense as just one independent aspect of a system as it relies upon a combination of human resources, technologies, and areas of operation. The best technology in the world will not prevent human error and the organization needs to adopt a corporate culture that has adversarial awareness. Organizations need to continually adjust and refine security countermeasures to protect against known and emerging threats. These measures raise the effective cost of intrusion to hackers. The goal is to the effort on the attacker’s side so difficult that they give up and move on toward easier prey.
As systems grow in complexity and connect to business and external networks, the number of potential security issues and their associated risks will grow as well. Gaining familiarity with the resources and methodologies made available by governments and standards organizations will ensure your system will be using best practices, will increase your likelihood of being able to adapt to an ever-changing cybersecurity challenge, and if a cyber intrusion occurs, it will enable outside expertise to come up to speed quickly and formulate a suitable response.
As these resources expand, and the industry adapts to improve its approach to threats, adopting a strategy in line with government recommendations will reduce the likelihood of being left behind.
Copyright Statement: The content of this website is intended for personal learning purposes only. If it infringes upon your copyright, please contact us for removal. Email: admin@eleok.com
